| PCI Network Requirements | Back Forward Print this topic |
Overview
For your organization to be PCI Compliant, your computer network must meet Requirements 1.2 and 1.3 regarding network security. Computers used by your staff to process credit cards must not be accessible to the public via your network, whether wired or wireless.
In addition, according to Requirements 11.1 and 11.2, your network must be tested for rogue wireless access points and must have network vulnerability scans performed every quarter.
Network Configuration
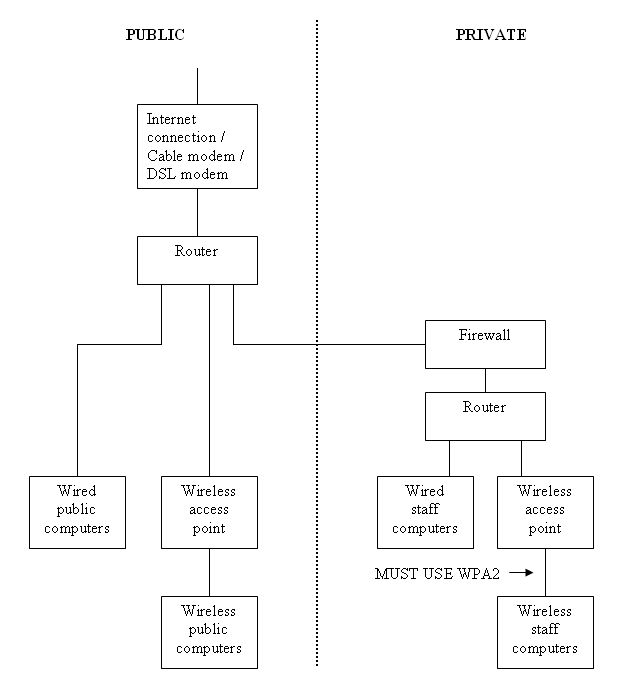
The diagram below shows a possible segregated network, where internal staff-use computers are protected from the Internet and from public computers at your location by a network firewall. The firewall allows the computers behind it to send and receive data while blocking unsolicited incoming messages.

While firewalls can be separate devices, most current routers have a firewall built in. Many routers also include a wireless access point, combining the devices shown in the diagram into a single box.
If you provide courtesy wireless access for your customers, this must be provided through a separate wireless access point than the one used by your staff. Internal wireless must be secured by WiFi Protected Access Version 2 (WPA2) for PCI compliance. You cannot use your public wireless network for credit card processing.
Any number of configurations and devices can support the network segregation required for PCI compliance. MyFBO.com recommends that you consult with a local network professional for assistance in configuring your location.
Wireless Access Point Testing
It is easily possible for employees or visitors to install a wireless access point on your private network. While your Information Security Policy will forbid such actions by employees, you must verify and document every quarter to assure PCI compliance.
This can easily be done by disabling your company's access points and then using a WiFi finder to test for rogue access points. If rogue access points are detected on your internal network, they must be removed. WiFi finders are readily available for less than $20 online and at many electronics stores.
You can also search for access points using your WiFi-enabled laptop computer or PDA. Verify that any unsecured access points are outside of your private network. Unsecured access may be from the public portion of your network, or from a neighboring business.
Alternatively, you may prefer to have your local network professional complete this task.
Network Vulnerability Scanning
External network vulnerability scanning must be completed and documented by a PCI-approved scanning vendor (ASV) each quarter. This type of scanning probes your private network perimeter (the firewall in the diagram above) to determine any network vulnerabilities.
There are many ASVs listed by the PCI Security Council. A search for free PCI scanning yielded numerous results, and we tried two of them. Both produced the needed compliance summary report. We did have a false start, however, because our firewall / router was set to "Block WAN Requests." This made our network completely invisible, causing the scan to fail. Make sure your firewall is set so that it can be detected from the internet, i.e. that it can be "pinged."
If an ASV asks for the IP address of your network, you can obtain this from your firewall. The IP address from which you are presently connected is 10.178.112.158
| Copyright © MyFBO.com [email protected] |
01/28/11 cli